You can use the reserved Jinja placeholders in supported Logpoint fields as templates to customize the output of a subject, message, or view. Go to Setting Up Alert Notifications and Creating an Alert Rule to learn more. These are the publicly available Jinja placeholders and Logpoint supported Jinja placeholders that are designated as internal use only.
Placeholders |
Description |
|---|---|
{{alert_name}}
|
Displays the name of the alert. |
{{alertrule_id}}
|
Displays the ID of the alert. |
{{attack_category}}
|
Displays the attack category associated with the alert. This corresponds to the tactics in Mitre ATT&CK Framework. |
{{attack_id}}
|
Displays the ID of the attack tags associated with the alert. This corresponds to the ID in Mitre ATT&CK Framework. |
{{attack_tag}}
|
Displays the attack tag associated with the alert. This corresponds to the techniques and sub-techniques in Mitre ATT&CK Framework. |
{{attack_info}}
|
Displays information about the attack, including attack_category, attack_tag, hash, attack_id, and _id (MitreAttack collection mongo Id). |
{{description}}
|
Displays the description of the alert. |
{{detection_timestamp}}
|
Displays the Epoch time when the alert was triggered. |
{{extra_info}}
|
Displays the information related to alert in a key-value format. |
{{format}}
|
Displays the timestamp format of the alert according to Year, Month, Day, Hour, Minutes, and Seconds. |
{{incident_id}}
|
Displays the ID of the incident generated by the alert. |
{{loginspect_ip_dns}}
|
Displays the IP of the Logpoint where the alert was triggered. |
{{logpoint_name}}
|
Displays the name of the Logpoint where the alert was triggered. |
{{log_source}}
|
Displays the log sources associated with the alert. |
{{risk_level}}
|
Displays the risk level of the alert. |
{{rows}}
|
Displays the log messages that triggered the alert. |
{{rows_count}}
|
Displays the total count of log messages that triggered the alert. |
{{search_link}}
|
Displays the link to search for alert related log. |
{{status}}
|
Displays the resolution status of incident generated by the alert. |
{{time_range}}
|
Displays the time-range of the alert in Epoch time. |
{{timezone}}
|
Displays the device timezone (UTC, GMT, ECT) |
{{type}}
|
Displays the query type of the alert. |
{{user_id}}
|
Displays the identity of the user account that triggered the alert. |
{{_id}}
|
Displays the object ID of the incident generated by the alert. |
Some examples of jinja commands that you can use to customize the output of a subject, message, or view:
Jinja template to display devices that sent logs:
{% for row in rows %} Device: {{row.device_name}} {% endfor %}
Jinja template to display severity-based message:
{% if risk_level == "medium"%} <p style = "color:yellow"> You need not take any action </p> {% elif risk_level == "high"%} <p style = "color:red"> Take action immediately </p> {% endif %}
Jinja template to display timezone of devices that sent logs:
{% for row in rows %} Time Zone: {{row.timezone}} {% endfor %}
Jinja template to send syslog notification with alert name and timestamp
{% for row in rows %} incident_name: {{alert_name}}; incident_ts: {{row.log_ts}}; {% endfor %}
Jinja template to display list of alerts and associated device ips:
{ "Summary": "Alert: {{alert_name}}", "description": "Alert fired from Log: {{rows|join(',', attribute='device_ip')}}", "raw_array": [ {% for row in rows %} { "col_ts": "{{row.col_ts}}", "device_ip": "{{row.device_ip}}" } {{ ", " if not loop.last else "" }} {% endfor %} ] }
Jinja template to write list of log datetime on a file:
echo -e "{% for row in rows %}{{row.log_ts|datetime('%B %d')}}{% endfor %}" >> /home/johndoe/file.txtThis command writes a list of log associated datetime on file.txt which is located inside /home/johndoe/.
Jinja template to display risk level of alerts:
{% for row in rows %} Risk Level: {{row.risk_level}} {% endfor %}
When using Pattern Finding queries in Logpoint, multiple logs that match the same pattern are combined into a single row. This search result has a more complex structure, and Jinja templates must be added differently.
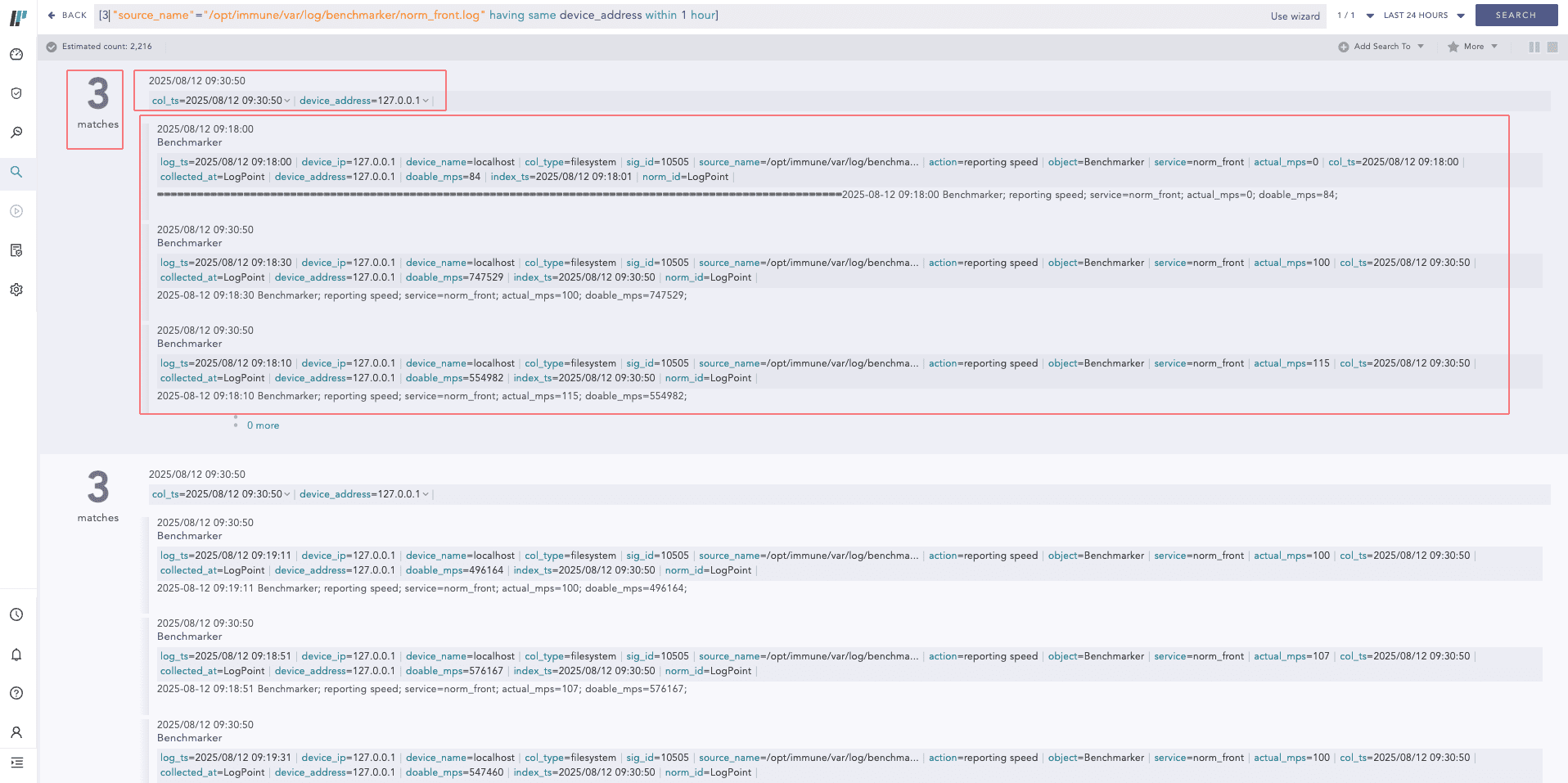
Search result when using Pattern Finding query¶
You must include common_info or participating_events in your Jinja templates to retrieve the correct values. If these structures are not used, the resulting alert notification may contain empty fields.
common_info — contains fields that are common across all logs in the result row.
participating_events — a list of individual logs that contributed to the Pattern Finding result.
Jinja template to display common information among all the logs:
{% for row in rows %} "col_ts": "{{ row.common_info.col_ts }}", "device_ip": "{{ row.common_info.device_ip }}" {% endfor %}
Jinja template to display common information along with individual log information:
{% for row in rows %} "col_ts": "{{ row.common_info.col_ts }}", "device_ip": "{{ row.common_info.device_ip }}", "logs": [ {% for event in row.participating_events %} { "caller_user": "{{ event.caller_user }}", "message": "{{ event.message }}", "source_address": "{{ event.source_address }}" } {% endfor %} ] {% endfor %
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support